By
Cynthia M. Lardner
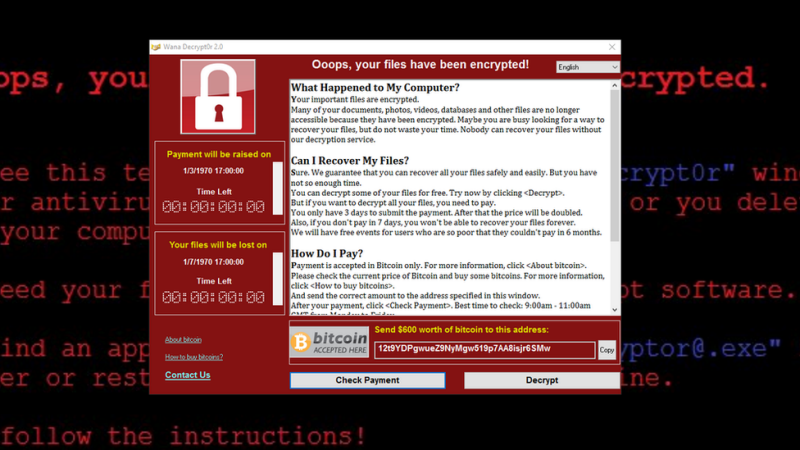
Cyber Security is always too much – too much money and too much time – until it just isn’t enough. Consider Friday’s news where a ransomware infection infiltrated organizations in 99 countries, including China and Russia. This should be enough to garner everyone’s attention about implementing simple rules for managing personal and professional privacy.
Photo/Webroot
I had the opportunity to interview an internationally-recognized cybersecurity expert who, for security purposes spoke only on the condition of anonymity, about preventive measures to thwart cyberattacks that employers should mandate and that individuals should voluntarily follow:
Is it true that anything transmitting information via the internet is capable of being hacked?
“Anything transmitted can be intercepted. Thus liable to hacking,”
Are there any limitations?
“There are no limitations.”
Where are the greatest vulnerabilities?
“There’re vulnerabilities everywhere.”
Whether you are an individual, a corporation, critical infrastructure or a government entity, isn’t the biggest vulnerability email accounts which are subject to spear phishing, i.e. sending emails that appear to be from an individual or business that you know?
“Email are valuable information for attackers. But there’re more. Targeting email through spear phishing emails is the primary method for hacking into a computer system. Spear phishing is very used nowadays, simply because it’s simple to implement. But no method can be defined as primary or the best. Each attack requires specific study and approach.”
Does the email need to include an attachment? If so, does the recipient need to open the attachment?
“Usually yes, but – again – it depends of the attack type.”
Are older systems more vulnerable to spear phishing?
“It’s not a rule. Each system comes with specific vulnerabilities. Something perfect doesn’t exist – since their made by humans.”
An email can include malware, viruses, spyware, adware, worms, or Trojans. How are these hacker tools different?
“Different names specify slightly different behaviours about functionalities and the way the backdoor works, e.g. auto-replication, data collected or not, data erased or not, etc.”
This is important information to consider when opening attachments as a report from the Anti-Phishing Working Group found that 2016 was the worst year in history for spear phishing scams – a 65% increase over 2015.
Let me give you a hypothetical. If a hacker interested in a public utility, they could visit the local coffee shop or restaurant patronized by its employees who mindlessly drop their business card in a fishbowl to win a free cup of coffee and swipe those cards. From there they could go through and identify persons of interest and engage in spear phishing, right?
“Absolutely right. This is just one good example of Social Engineering; that is – nowadays – the most dangerous attack.”
Does hacking a computer or even a smart phone give the hacker access to more than just the initial device targeted? For instance, if my computer was hacked and I send an email to another computer do I infect that system?
“It depends. If the worm has auto-replication capabilities YES.”
I read that Target, Sony Pictures, the Democratic National Committee (DNC) and the U.S. Office of Personnel Management (OPM) were attacked because they relied on passwords alone for authentication. How important is the complexity, duplicity and age of passwords?
“It’s very important. But keep in mind that even a very strong password can be hacked using specific attack types – like brute force or dictionary attacks.”
Is it true that even eight character passwords can be hacked in under a second?
“Yes, even less.”
What is a dictionary password hack?
“A dictionary-based attack uses a pre-filled file that contains thousands or hundreds of thousands, or more words. Each word is used as password tentative.”
Verizon’s 2016 Data Breach Investigations Report found that “63 percent of confirmed data breaches involve using weak, default or stolen passwords.” What is your advice about passwords?
“Use at least a 16 characters password. And change it every week.”
Can you offer an example and explanation of a good password?
“%-xGaY%p2Rv@Pcx_! A password should be 16 characters minimum and include symbols, numbers, lowercase and uppercase characters.”
This means that you are inviting unwanted intruders into your business or home when you use the pre-installed default passwords, such as “admin” or “1234”, or when a single password is used for multiple accounts.
What is a multi-factor authentication (MFA) solution?
“It means that one password is no more enough to be authenticated.”
Can you give me an example?
“A 2 factor authentication, for example, requires, first, a password and then, second, a randomly-generated code that changes every X seconds.”
Is MFA an effective strategy?
“Better than only one password, for sure. Online banks, for example, nowadays use this mechanism by default.”
Would you agree that protecting one’s email addresses is almost or as important as protecting one’s passwords?
“On password-based systems, password protection should always been considered at first place, from user perspective. Possible systems vulnerabilities can be managed only by ISP itself (not the user).”
How about another hypothetical. An employee uses their personal email address on LinkedIn. If a hacker wanted to hack into the company they worked for they could spear phish their home computer, which is likely used to login to work. Under what circumstances would that give a hacker access to the company’s system?
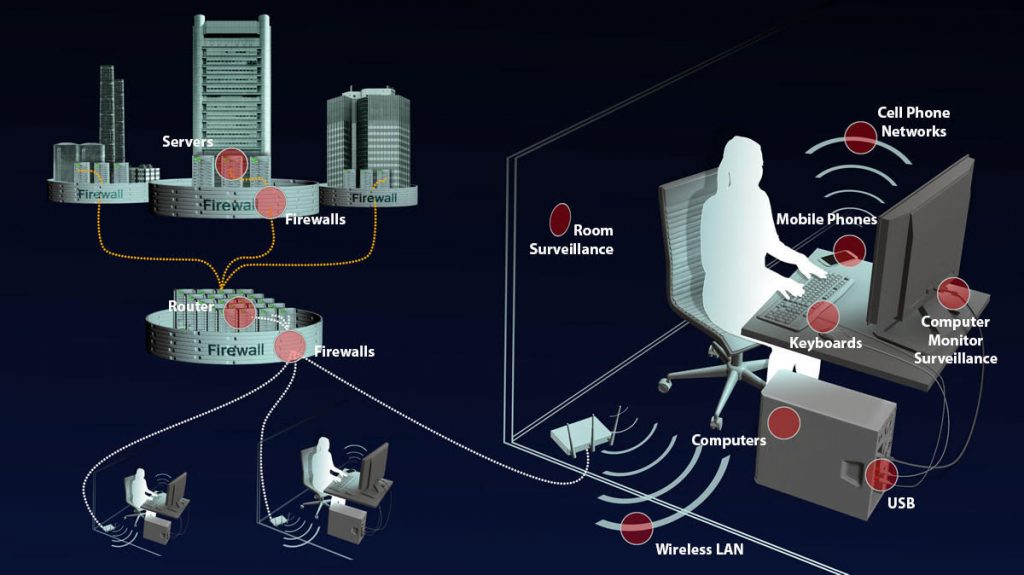
“Accessing a company network is in general less simple than accessing a home computer. Even if you already attacked/infected a company device, you have to consider that the company has in place network barriers (like firewalls, IDS, etc.) that may prevent to access easily from external network to internal network. That way, usually, modern backdoors prefer communications only “moving” FROM attacked device (internal network) TO remote server (external network). The IN-to-OUT transmission is always better than OUT-to-IN.”
This is where I am confused. Once hacked, access to the internet signal is obtained. Does this impact hacking other systems? Does it matter if an individual has separate devices and computers for personal and professional use?
“When a system is hacked, it means that something is “going to happen”. Connecting to the Internet in order to transfer something is most probably something that will happen, but it’s not mandatory (you may just want to duplicate data and keep them on the disk, for a later physical retrieval, or you may want to delete/alter something, or just opening a communication port for an OUT-to-INT communication, etc.). During an attack, the attacker wants to minimise the impact of suspects around 0%, so the idea that other systems may be impacted or “considered” during the attack… it’s something bad. An attack is usually studied, tested and then implemented SPECIFICALLY for the target device. No other systems should be even touched to accomplish this. Of course, large scale attacks require multiple systems to be compromised.”
Photo/NSA
Do you have any thoughts on using Wi-Fi at home or in public?
“If you want to have a “safe” network (at home or at work)… do not use WiFi. If I was a hacker couldn’t I login into a public Wi-Fi and intercept signals from all devices logged onto the internet connection? If you connect as attacker to a public WiFi, you can actually retrieve almost everything (visited websites, user, password, PINS) that users think “it’s safe”.
What is your general advice about using Wi-Fi?
“If available, the use of a Wi-Fi network is probably one of the first attempts to try an attack.”
Restraint on the use of Wi-Fi is statistically supported. According to a report published by the Chertoff Group:
- Mobile web adoption is growing 8 times faster than web adoption did in the 1990s and early 2000s.
- By the end of 2017, over two billion mobile phone or tablet users will make some form of mobile commerce transaction.
- By 2018, 25% of corporate data traffic will bypass the corporate network and flow direct from mobile device to the cloud.
- 84% of people have experienced difficulty completing a mobile transaction.
- 62% of “checkout abandonments” in mobile commerce happen due to friction in the login process.
I have another hypothetical for you. A personal smart phone has been hacked. If the hackers have installed key loggers or other malware doesn’t this mean they can see every keystroke made, including password and messages believed to be encrypted, whether by specialized software or common apps such as WhatsApp?
“Yes. A malware running directly on the device doesn’t care about encryption: it is installed ON the system, so it’s capable to read everything BEFORE encryption (or after decryption).”
What is your advice on selecting a search engine? Does Google, Yahoo and Bing create a greater vulnerability than TOR?
“Everything is traced and monitored. Search engines and the TOR network, as well.”
A lot of critical infrastructure relies heavily on legacy or outdated software that was never intended to be used with more modern technology to control their product. A lot of legacy software lacks the ability to manually override a cyberattack. This is a major issue in the United States and in some parts of the European Union where public power and transportation are controlled by thousands of companies many of which lack the resources to address vulnerabilities. Many companies have failed to make capital investments in its computer systems preferring to link legacy software to newer technology thereby is opening the floodgates for cyberattacks. The U.S. Department of Energy published a report saying that the nation’s electrical grid “faces imminent danger” from cyber-attacks. The report concluded that grid modernizations would require a total investment ranging from $350 to $500 bn.
What are the drawbacks to linking newer technology to older Linux or legacy systems? Where is the greatest vulnerability when two systems are linked together?
“When a system is “connected” it automatically becomes vulnerable. It’s not a matter of old or new technology, it’s a matter of how the system is “exposed”. But EVERY system is exposed in some way, or it cannot serve anything.”
The Cloud is not less secure than an internal system. The vulnerability is in the internet or intranet connection. Systems managers should focus on securing cloud workloads and not the Cloud. The cloud does not make a system less secure, it’s when the internet or intranet connection has a vulnerability that opens the Cloud to attacks.
Are there any signs the people should watch for that are indicative of hacking?
“A well performed attack, leaves no trace. If we speak about people, 99% of them are vulnerable and not capable to understand that they’ve been hacked. Speaking about companies, the percentage changes, but not so much.”
As it’s been in the news lately, one last question; how are other things like the television, thermostat and garage door opener hacked?
“Again, if something is “connected”… it becomes vulnerable. The IOT – Internet of Things – will be one of the most catastrophic phases of this era, from hacking, information theft and safety point of view. It has been already proved that it’s possible to completely take control of a modern car, hacking it from thousands of miles of distance. And this is only the beginning.”
Another area in which companies can be proactive is by employing multiple-level redundancy. This means you have created multiple back-up copies of your data to prevent loss in the case of a single disk or server failure and that the data is stored across multiple geographic locations.
When considering whether to make organizational or personal internet safety changes, along with today’s immense ransomware attack consider these statistics:
- 70% of U.S. critical infrastructure suffered a cyberattacks in 2016.
- The UK’s National Cyber Security Centre revealed that Britain was threatened by 188 high-level cyber-attacks in just three months.
- The average attack on a financial institute costs $20.8 mm even though the response time has been shortened to an average of 17.5 hours.
- Ransomware attacks rose by 50% in 2016 with 61% of victims now being companies with less than 1,000 employees.
- Up to 286 mm viruses are detected annually by Symantec.
For more information visit the Federal Bureau of Investigation’s webpage on cyber security and the NIST Cybersecurity Framework, which provides a policy framework on computer security guidance to assist private sector organizations in assessing and improving their ability to prevent, detect, and respond to cyber-attacks.
The author with former United Nation Secretary-General Ban Ki-moon at the inauguration of the new ICC complex on April 19, 2016
Cynthia M. Lardner
Cynthia M. Lardner is an American journalist living in The Hague. She is a contributor to Tuck Magazine, E – The Magazine for Today’s Executive Female Executive, and the International Policy Digest. Her blogs are read in over 37 countries. As a thought leader in the area of foreign policy, her philosophy is to collectively influence conscious global thinking. Ms. Lardner holds degrees in journalism, law, and counseling psychology.
Sources
Chertoff, Michael, “8 Ways Governments Can Improve Their Cybersecurity”, April 25, 2017, Harvard Business Review.
Knake, Robert, “A Cyberattack on the U.S. Power Grid”, Contingency Planning Memorandum 31, April 2017, Council on Foreign Relations.


No Comments Yet!
You can be first to comment this post!