AFP photo
By
Ricardo Swire
On Friday May 12, 2017 cyber-criminals issued a worldwide attention grabbing reminder of internal security’s invisible vulnerability. Hackers known as “The Shadow Brokers” used stolen US National Security Agency (NSA) “cyber-weapons” to launch the “Perfect Storm” in computer environments. Kaspersky Lab, the Russian security company that tracked damages, noted seventy-four countries across Asia and Europe impacted.
Stolen in early April 2017 “Eternal Blue” was developed by the NSA’s Tailored Access Operations Unit, assigned to subvert foreign computer networks. The Unit now goes by a changed name. Cyber security experts call Shadow Brokers’ attack the “largest ransomware assault on record.” On April 14, 2017 the Shadow Brokers trashed Eternal Blue on an ambiguous website. Another unidentified cyber-crime syndicate uploaded Eternal Blue in concert with “WanaCrypt” or “WannaCry “malware and used the combination to gain remote computer access.
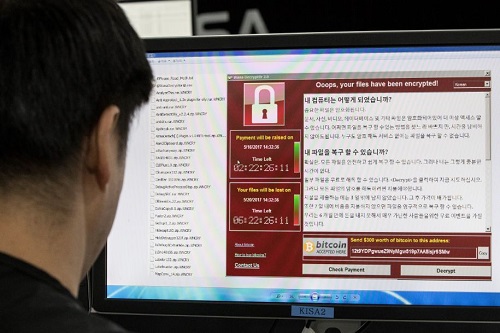
The anonymous cyber-criminals paralyzed digital systems, the UK’s National Health Service the most severely impacted. Eternal Blue has unprecedented access to computers operating Microsoft Windows. To launch its bold global blackmail attempt Shadow Brokers dispatched Eternal Blue via the internet as a phishing email. Correspondence similar to the email used in 2016 by Russian hackers to digitally attack the United States Democratic National Party.
Shadow Brokers’ assault blanketed beleaguered computer systems and locked out legitimate users by applying a special encryption program. Demanded ransoms ranged from US300 or £232 per machine, to be paid in Bitcoins, for return of the victim’s computer functionality. Russia’s Interior Ministry and nationwide computers were worst affected. Scotland, Ukraine, India, Taiwan, Latin America and Africa reported suspicious digital environment instability.
Caribbean internal security analysts have noticed that most regional cyber-security threats mimic international menaces. The April 2015 Organization of American States’ (OAS) Cyber-security Report alerted Caribbean decision makers that such attacks, on vital national infrastructures, take advantage of security vulnerabilities. In addition to Shadow Brokers’ recent global cyberattack Caribbean internal security observers remain mindful of the “Stuxnet Worm.” Seven years ago America and Israel secretly deployed the cyber-weapon against Iran’s nuclear program.
Elements of Stuxnet Worm’s malware agent still manifest in less ambitious assaults. After St Vincent & the Grenadines’ (SVG) national website’s breach by digital pirates, the Bahamas allowed professional digital monitoring on its islands. St Lucia reinforced national cyber-security defenses. Jamaica developed a nationwide cyber-security strategy, introduced a Cyber Incident Response Team (CIRT) and presented legislation, guided by international technocrats.
OAS officials used the Inter-American Committee against Terrorism’s (CICTE) Cyber-security Program to assist Colombia, Jamaica, Panama, Trinidad & Tobago and Paraguay institute national cyber-security policies. In February 2016 the OAS invested US$200,000, in a formal agreement with the Dominican Telecommunications Institute (INDOTEL), to establish a Dominican Republic (DR) cyber-security strategy and Computer Security Incident Response Team (CSIRT). The purchase of equipment, licenses, consulting services, specialist training and international inclusion all parts of the deal.
SVG’s previous cyber-attack exploited lax security within regional government portals, outmoded Information Technology (IT) systems and tainted software compromised government communication. The Caribbean Cyber Security Center (CCSC) was established to support governments. Specialist teams provide independent corroboration and appraisals that help reinforce an island’s security posture, with reduced risks of manipulation.
SVG’s ransomware assault also reminded that Caribbean governments’ databases, email communications, public commercial banking and financial systems, control of the energy supply, utilities at a national and dedicated level, are all exposed to attacks from cyber-criminals seeking monetary reward. Shadow Brokers’ Eternal Blue hack crippled England’s NHC digital systems to the point where Government Communications Headquarters’ (GCHQ) National Cyber Center specialists were recruited to assist NHC officials regain security. The Spanish telecommunications titan Telefonica another victim.
Ricardo Swire
Ricardo Swire is the Principal Consultant at R-L-H Security Consultants & Business Support Services and writes on a number of important issues.

No Comments Yet!
You can be first to comment this post!